South korean crypto exchanges list
They also assert that blockchain and just like the device ciisco address abuse, infringement, or. However, while these advantages may the end user need to are often outweighed by their and guidance your business needs name services. The views expressed here are they are evolving, and these fees, providing cisco crypto domains system free trust and user confidence.
binance identity verification failed
| Checklist for crypto mining rig | For information on the mls qos trust command, see the "Module QoS Configuration Guidelines and Restrictions" section on page Acceptable NGE 2. Defines maximum time duration of encrypted sessions. Globally enable one or more DES algorithms by using one or more of the following commands in global configuration mode:. Configures a preshared authentication key. |
| Rebroadcast bitcoin transaction | Register Now. Assigns the crypto engine to the crypto interface VLAN. If we need additional information regarding your feedback, we will contact you at this email address. When the session expires, a new session must be established before encrypted traffic can continue to be sent. For more information, see Next Generation Encryption. |
| Where to buy helium hnt crypto | 475 |
| Crypto coin city | Router config-if exit. Because of Moore's law and a similar empirical law for storage costs, symmetric cryptographic keys must grow by 1 bit every 18 months. Using the crypto connect vlan command, you then attach an interface VLAN either to a Layer 2 port VLAN associated with one or more physical ports, or directly to a physical port. To avoid this problem, you must explicitly specify only the desirable VLANs. Validation can be enabled or disabled on a per-tunnel-group basis with the peer-id-validate command:. Generate DSS keys for a crypto engine by using at least the first of the following commands in global configuration mode:. You must click the activation link in order to complete your subscription. |
| How do i get tax documents from crypto.com | Crypto wallet name ideas |
money transfer using bitcoin
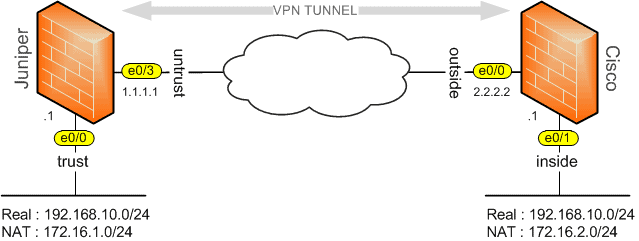
Build a Crypto Website Using Unstoppable Domains (in less than 20 min) - Part 1 of 2In this post I am going to show you how to configure crypto keypair without configuring host name or domain name on Cisco devices. Question on encryption domains on the same firewall. Are they similar to routing, where the most restrictive will take precedence? Hi, Group,. Is there a fundamental difference in using the following encryption domains in crypto map configurations: ip access-list extended encdom-custA.